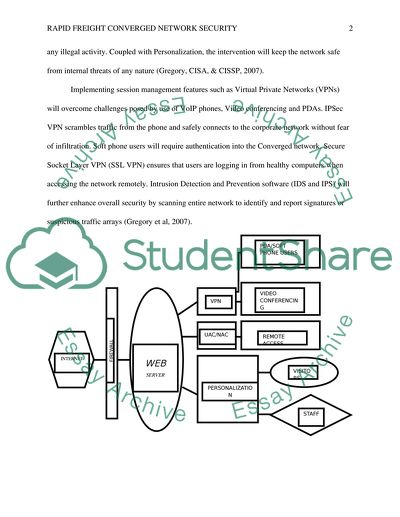
Rapid Freight Converged Network Security Case Study. Retrieved from https://studentshare.org/information-technology/1604371-case-study-archetcectural-diagram
Rapid Freight Converged Network Security Case Study. https://studentshare.org/information-technology/1604371-case-study-archetcectural-diagram.