StudentShare


Our website is a unique platform where students can share their papers in a matter of giving an example of the work to be done. If you find papers
matching your topic, you may use them only as an example of work. This is 100% legal. You may not submit downloaded papers as your own, that is cheating. Also you
should remember, that this work was alredy submitted once by a student who originally wrote it.
Login
Create an Account
The service is 100% legal
- Home
- Free Samples
- Premium Essays
- Editing Services
- Extra Tools
- Essay Writing Help
- About Us
✕
- Studentshare
- Subjects
- Information Technology
- Network Security Concepts
Free
Network Security Concepts - Assignment Example
Summary
This paper 'Network Security Concepts' tells that The host computer (192.168.1.105) asks the DNS server (192.168.1.1) to resolve cqu.edu.au in the 39th row, which it does and then later returns the numerical IP address of webfuse.cqu.edu.au to be 192.168.1.1 in the 41st row, destination column. …
Download full paper File format: .doc, available for editing
GRAB THE BEST PAPER95.9% of users find it useful
- Subject: Information Technology
- Type: Assignment
- Level: High School
- Pages: 4 (1000 words)
- Downloads: 0
- Author: wilfredo65
Extract of sample "Network Security Concepts"
Network Security Concepts Affiliation a. Create a Cisco IOS standard IP access list that allows IP packets from all hosts from the 142.16 network
access-list 0 permit 142.16.0.0 0.0.255.255
b. Create a Cisco IOS standard IP access list that allows IP packets from all hosts from the 142.16 network except hosts on the subnet 142.16.11
access-list 16 permit 142.16.0.0 0.0.255.255
access-list 11 deny 142.16.11.0 0 0.0.255
c. Create a Cisco IOS extended IP access list that allows any host to access a web server on TCP port 80 whose IP address is 142.16.11.50
access-list 105 permit tcp 0.0.0.0 255.255.255.255 142.16.11.50 0.0.0.0 eq 80
d. Create a Cisco IOS extended IP access list that allows any host to access the internal SMTP server at 142.16.11.55 (tcp port 25), and the DNS servers at 142.16.11.174 (TCP and UDP port 53)
access-list 105 permit tcp 0.0.0.0 255.255.255.255 142.16.11.55 0.0.0.0 eq 25
access-list 105 permit tcp 0.0.0.0 255.255.255.255 142.16.11.174 0.0.0.0 eq 53
access-list 105 permit udp 0.0.0.0 255.255.255.255 142.16.11.174 0.0.0.0 eq 53
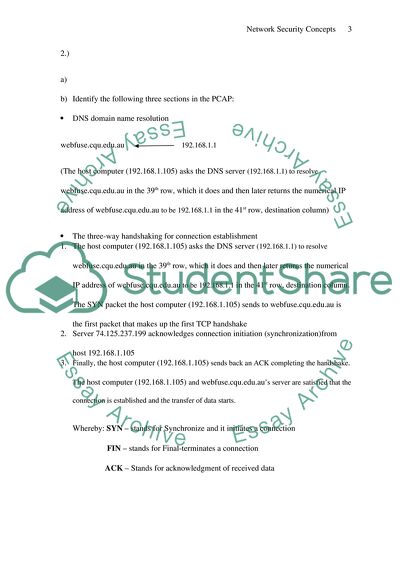
2.)
a)
b) Identify the following three sections in the PCAP:
DNS domain name resolution
webfuse.cqu.edu.au 192.168.1.1
(The host computer (192.168.1.105) asks the DNS server (192.168.1.1) to resolve webfuse.cqu.edu.au in the 39th row, which it does and then later returns the numerical IP address of webfuse.cqu.edu.au to be 192.168.1.1 in the 41st row, destination column)
The three-way handshaking for connection establishment
1. The host computer (192.168.1.105) asks the DNS server (192.168.1.1) to resolve webfuse.cqu.edu.au in the 39th row, which it does and then later returns the numerical IP address of webfuse.cqu.edu.au to be 192.168.1.1 in the 41st row, destination column. The SYN packet the host computer (192.168.1.105) sends to webfuse.cqu.edu.au is the first packet that makes up the first TCP handshake
2. Server 74.125.237.199 acknowledges connection initiation (synchronization)from host 192.168.1.105
3. Finally, the host computer (192.168.1.105) sends back an ACK completing the handshake. The host computer (192.168.1.105) and webfuse.cqu.edu.au’s server are satisfied that the connection is established and the transfer of data starts.
Whereby: SYN – stands for Synchronize and it initiates a connection
FIN – stands for Final-terminates a connection
ACK – Stands for acknowledgment of received data
Connection termination
FIN – stands for Final-terminates a connection
Row 218- 11.681400000 74.125.237.220 192.168.1.105 TCP 54 [TCP Retransmission] https > 52521 [FIN, ACK] Seq=1 Ack=1 Win=667 Len=0
c)
Packet No.
Time
Source
Destination
Protocol
Info
39
2.344129000
192.168.1.105
192.168.1.1
DNS
Standard query 0xb5d8 A webfuse.cqu.edu.au
Explanation: The host computer (192.168.1.105) asks the DNS server (192.168.1.1) to resolve webfuse.cqu.edu.au
45
2.403044000
192.168.1.105
138.77.5.135
TCP
http [SYN] Seq=0 Win=8192 Len=0 MSS=1460 WS=4 SACK_PERM=1
Explanation: It initiates the connection between the host computers (192. 168. 1. 105) and the server at 138.77.5.135
49
2.502009000
74.125.237.199
192.168.1.105
TCP
https > 52481 [ACK] Seq=1 Ack=2 Win=661 Len=0 SLE=1 SRE=2
Explanation: server 74.125.237.199 acknowledges connection initiation (synchronization)from host 192.168.1.105
52
2.504516000
74.125.237.218
192.168.1.105
TCP
https > 52517 [FIN, ACK] Seq=1 Ack=1 Win=664 Len=0
Explanation: Server at 74. 125. 237. 218 sends an acknowledgement to host at 192.168.1.105 to end the connection
d) Frame number 64.
I was able to identify the frame from the http 404 error thrown, to arrive at the retrieved web page and by clicking on the frame packet row I was able to retrieve the paragraph with the message “The requested URL /YourStudentNumber.html was not found on this server”.
3.) Introduction
Computers running Windows operating systems are affected by a new malware named Flasher which is a Trojan horse, spread by a targeted attack. A Trojan horse is software that secretly gets installed in the host machine principally through malware programs to enable its designer (mostly hackers with destructive intentions) to gain full control of the machine in question, and is capable of exposing sensitive information to unauthorized and unintended audiences and/or even destroy the entire system .Trojan horse, and more specifically flasher, is spread through emails sent to selected individuals. This report investigates the details of Flasher Trojan behavior and propagation techniques and then later suggests ways through which the network could be protected from such attacks.
Flasher Trojan Behavior and Propagation Techniques
Flasher Trojan horse malware basically exploits the vulnerabilities of the Windows operating system to spread on the wide area networks, better known as the internet (Exterminate Lab 2014). Flasher creates unique identifiers in memory which can be updated and be varied to mimic legitimate file names (Exterminate Lab 2014). In this manner, malware infected files are easily camouflaged to take the same file names as the obviously trusted ones, enabling them to stay in the system longer and undetected (Exterminate IT 2014). This malicious software, it has been found out, can be used to steal vital information from targeted machines and/or even inflict serious damage to the infected machine. It has been found that they can render the operating system useless or disrupt its operations, steal vital private information like pin codes, passwords, credit card numbers among others, direct all web searches from an infected computers to malicious websites, gains complete control of the infected machine and can even introduce more malicious programs like viruses and worms or even aid to send out spam messages, and finally it dramatically slows down the infected machine (Exterminate IT 2014).
It can be spread through infected email attachments, peer to peer file exchange, instant messaging and through adult-related sites (Free Spy Check 2014). The primary propagation methods include social networks (access to third party applications and software) and pirated software which might be containing malicious codes (Combo Fix 2013). Also the following are some of the ways that the Flasher malware can be propagated in the system: emails (mostly spread through attachments), removable media (mostly USB sticks) and finally, through infected websites (Combo Fix 2013). It has also been observed that flash based advertising aid in then spread of the flasher Trojan malwares (Security FAQS 2012).
The Protection of the Network from Flasher Trojan Malwares
Due to the harmful effects of the flasher Trojan malwares as discussed above, it is important to protect and/or remove these damaging programs from the system. The system can be scanned and if the flasher Trojan malware is detected be removed together with the clones, aliases and related files (Free Spy Check 2014). It is advisable to remove all folders, files and keys and their value of the register for windows (Exterminate Lab 2014). To achieve the above, it is highly recommended that registry entries associated with cracks and hacks be repaired, fully system scan for the malware be done on the machine, the system junk be cleaned out to get rid of temporary folders and files, PC device drivers be updated regularly, when need be restore the system changes through use of the undo button, uninstall and re-install the cracks and hacks associated with flasher.exe, system file checker be run on windows, all updates (windows) be installed and finally, if need be a new windows installation must be performed (Solvusoft 2014).
.
References
Combo Fix 2013. How malware attacks and spreads in your computer. [Accessed on 15 August 2014]. Available from
Exterminate IT 2014. Location of Flash.in and Associated Malware. [Accessed on 15 August 2014]. Available from
Exterminate Lab 2014. Flasher. [Accessed on 15 August 2014]. Available from < http://www.exterminatelab.com/remove-flasher-virus>
Free Spy Check 2014. Flasher.exe Removal. [Accessed on 15 August 2014]. Available from
Security FAQS 2012. How Is Malware Spread through Flash Based Advertising. [Accessed on 15August 2014]. Available from
Solvusoft 2014. [Accessed on 15 August 2014]. Available from
Read
More
CHECK THESE SAMPLES OF Network Security Concepts
Network Security
The author gives a large overview of Jackson, Chris "network security auditing", Harrington Jan "network security: A Practical approach", Douglas Comer “Computer Networks and Internets” and other works on the topic of network security.... Current annotated bibliography includes Winkler Vic "Securing the Cloud: Cloud Computer Security Techniques and Tactics", Chey Cobb "network security for dummies", Cole Eric "Networking security bible", Donahue Gary Network Warrior" and other books on the stated topic....
18 Pages
(4500 words)
Annotated Bibliography
Network Security Risk Assessment
network security Risk Assessment network security Risk Assessment Introduction Advancement in technology has resulted to the development of innovative computing systems which have facilitated the functions of various organizations and institutions.... he increasing complexity of information systems has resulted to information security threats .... The increasing complexity of information systems has resulted to information security threats which have infringed the right of individuals to privacy of information....
9 Pages
(2250 words)
Term Paper
Privacy-Enhancing Security Mechanisms
There exist many privacy enhancing security mechanisms that ensure secure delivery of data to the intended location.... In this paper, we will discuss the technique to design a reliable and efficient privacy-preserving scheme in order to ensure increased security of data over the network.... Problem Statement The problem statement for the research paper is: "Design and analysis of privacy-preserving network and cryptographic protocols" Conceptual Framework Aim of the Research In realistic networked environments, data security is the main focus of the management....
3 Pages
(750 words)
Research Proposal
Network Security setup
Running Header: network security setup Part Security layers outline for Richman investment IT infrastructure domain
... ecuring organization's data from external threats has been one of the major goals of network security since the inception of the TCP/IP protocol that generated the internet.... network security, Firewalls, and VPNs.... The necessary security measure here is installation of updated anti-spyware and antivirus....
7 Pages
(1750 words)
Research Paper
Impact of the Virtual Private Network on Businesses
Handbook of Information Security: Key concepts, Infrastructure, Standards, and Protocols.... A virtual private network (VPN) enables the developing or building of private networks across the internet, enabling security and tunneling of non-TCP/IP protocols; for instance, remote users uses VPNs to give connect over a public medium like the Internet instead of expensive permanent means.... PNs employ four major basics from the IPSec security protocols; algorithms required for encryption, secure key exchange, key exchange mechanisms, and SA definitions and maintenance....
5 Pages
(1250 words)
Research Paper
Network Security And Management
In'network management,'fault management'is the set of functions that detect, isolate, and correct malfunctions in a telecommunications network, compensate for environmental changes, and include maintaining and examining'error'logs, accepting and acting on error'detection'notifications, tracing and identifying faults, carrying out sequences of diagnostics tests, correcting faults, reporting error conditions, and localizing and tracing faults by examining and manipulating'database'information....
3 Pages
(750 words)
Article
Information Security Management
he network security element of subnetting improves security by way of splitting an Internet Protocol or IP address anywhere within its 4-byte (or 32-bit) address.... This assignment "Information security Management" discusses data miners that have also had serious violations of privacy.... In view of the fact that such information does not include the patient's name, phone number, address, and social security number, the idea that a patient's privacy would be violated may seem far-fetched....
8 Pages
(2000 words)
Assignment
Concept of Network Security
onclusionOverall, information about basic Network Security Concepts has developed many recognized cybersecurity practices and methods that are used to create a viable network security management strategy.... The paper "Concept of network security" suggests that understanding network security is identified as the inclusion of multiple layers used to defend the network.... At each level of network security, different controls and policies promote access to a particular security network....
5 Pages
(1250 words)
Case Study
sponsored ads
Save Your Time for More Important Things
Let us write or edit the assignment on your topic
"Network Security Concepts"
with a personal 20% discount.
GRAB THE BEST PAPER

✕
- TERMS & CONDITIONS
- PRIVACY POLICY
- COOKIES POLICY